Contact Form 7 can be installed directly from the WordPress plugin repository. If you search for “contact form 7”, you’ll be able to find the plugin along with a variety of add-ons. Install the Contact Form 7 plugin from the WordPress plugin repository. Contact Form 7 is one of the most popular contact form plugins for WordPress. It’s also one of the oldest that’s also easy to use. In fact, many WordPress themes come with pre-made styles for Contact Form 7. As popular as Contact Form 7 is, it’s not uncommon for users to encounter a problem with their contact form not sending email. WordPress Contact Form 7 Vulnerability Lets come straight to the important point – Those using the Contact Form 7 plugin are advised to update to version 5.3.2 as soon as possible for added security. Reports on vulnerabilities in WordPress plugins have become a daily occurrence and, although most of these. Contact Form 7 Mail Does not encode pound sign. Started by: pmelzer23. 1; 0; 18 hours, 42 minutes ago. Form sends but success message does not pop up help. Started by: cece101. 2; 1; 11 hours, 31 minutes ago. Takayuki Miyoshi. Combining Redirections and Google Analytics Events. Started by: menxie. 1; 0; 22 hours, 12 minutes ago.
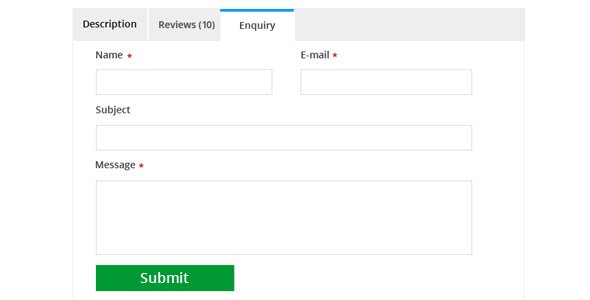
Description
Contact Form 7 can manage multiple contact forms, plus you can customize the form and the mail contents flexibly with simple markup. The form supports Ajax-powered submitting, CAPTCHA, Akismet spam filtering and so on.
Docs and support
You can find docs, FAQ and more detailed information about Contact Form 7 on contactform7.com. When you can’t find the answer to your question on the FAQ or in any of the documentation, check the support forum on WordPress.org. If you can’t locate any topics that pertain to your particular issue, post a new topic for it.
Contact Form 7 needs your support
It is hard to continue development and support for this free plugin without contributions from users like you. If you enjoy using Contact Form 7 and find it useful, please consider making a donation. Your donation will help encourage and support the plugin’s continued development and better user support.
Privacy notices
With the default configuration, this plugin, in itself, does not:
- track users by stealth;
- write any user personal data to the database;
- send any data to external servers;
- use cookies.
If you activate certain features in this plugin, the contact form submitter’s personal data, including their IP address, may be sent to the service provider. Thus, confirming the provider’s privacy policy is recommended. These features include:
- reCAPTCHA (Google)
- Akismet (Automattic)
- Constant Contact (Endurance International Group)
Recommended plugins
The following plugins are recommended for Contact Form 7 users:

- Flamingo by Takayuki Miyoshi – With Flamingo, you can save submitted messages via contact forms in the database.
- Bogo by Takayuki Miyoshi – Bogo is a straight-forward multilingual plugin that doesn’t cause headaches.

Translations
You can translate Contact Form 7 on translate.wordpress.org.
Blocks
This plugin provides 1 block.
- Contact Form 7
Installation
- Upload the entire
contact-form-7folder to the/wp-content/plugins/directory. - Activate the plugin through the Plugins screen (Plugins > Installed Plugins).
You will find Contact menu in your WordPress admin screen.
For basic usage, have a look at the plugin’s website.
FAQ
Do you have questions or issues with Contact Form 7? Use these support channels appropriately.
Reviews
Updated on
WordPress Contact Form 7 Vulnerability
Table of Contents [TOC]
- WordPress Contact Form 7 Vulnerability
Lets come straight to the important point – Those using the Contact Form 7 plugin are advised to update to version 5.3.2 as soon as possible for added security.
Reports on vulnerabilities in WordPress plugins have become a daily occurrence and, although most of these flaws are detected early, this is not the only key factor to avoid their exploitation.
In this article, We’ll explain more about contact form 7 exploit and way to fix the Contact Form 7 privilege escalation vulnerability in WordPress.
The patched version was released early today, Wednesday, December 17, 2020. If your site is one of the many sites using Contact Form 7, we strongly recommend that you update to version 5.3.2 as soon as possible.
A cybersecurity firm has reported the finding of a new flaw in Contact Form 7, a popular plugin for creating multiple forms. If exploited, this vulnerability would allow threat actors to escalate privileges on the vulnerable site.
RELATED PLUGIN VULNERABILITIES FOUND:
A hacker who successfully exploited the vulnerability could perform various malicious activities, such as modifying content, redirecting visitors to unknown sites, stealing information, and could even take full control of the target site and block access to the legitimate administrator.
As if that weren’t enough, Google could detect this anomalous behavior and arbitrarily block the site, complicating the recovery process.
Contact Form 7 is a popular plugin active on more than 5 million WordPress sites that was updated yesterday to version 5.3.2. This update includes a patch that addresses a severe vulnerability, such as Unrestricted File Upload, which would allow an attacker to perform various malicious actions, including taking control of a site or the entire server hosting the site. Over the years, it has been revealed to have several major security flaws. Unsurprisingly, these vulnerabilities have caused many sites to be hacked.
This popular WordPress plugin is used to add contact forms on a site and manage the contacts that users leave after completing the form.
Contact Form 7 Plugin Vulnerability In WordPress
Contact Form 7 content is stored in a folder called wp-content on every WordPress site; This folder contains data related to the content of the site but does not store confidential information. According to cybersecurity specialists, if a hacker manages to access files outside of this folder, the targeted user faces multiple security problems due to the confidential nature of their content.
The Contact Form 7 vulnerability allows hackers to inject malware in WordPress uploads directory/folder; specifically the /wp-content/uploads/wpcf7_uploads/ folder. Once the file is uploaded, the hackers can then take over control of the entire website.
Therefore it is important to scan your wordpress site using a malware scanner and then a clean it to remove malware from wordpress website
Only site administrators are supposed to be able to modify the content of forms created with Contact Form 7, a feature controlled by a parameter called capability_type, which defines user permissions. A security flaw in this parameter allows any user, regardless of their privilege level, to make changes to the forms.
A second attack scenario can be triggered by modifying the type of files accepted in a Contact Form 7 form. Some forms ask users to upload files in various formats (PDF, JPG, GIF, among others); By exploiting the vulnerability, a threat actor could alter the plugin configuration to be able to upload executables (PHP, ASP and others) to the target site and deploy other attack variants, cybersecurity specialists mention.
The report was sent to the plugin developers, who fixed the bug with the release of version 5.0.4. The International Institute for Cyber Security (IICS) strongly advises administrators of vulnerable deployments to update to the latest version as soon as possible.
The vulnerability, classified as CVE-2020-35489, affects version 5.3.1 and earlier of the plugin. In fact, it is estimated that around 70% of active Contact Form 7 users are exposed to this flaw.
CVSS v3.1 Severity and Metrics:
Base Score: 10.0 CRITICAL
Vector: AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
Impact Score: 6.0
Exploitability Score: 3.9
Attack Vector (AV): Network
Attack Complexity (AC): Low
Privileges Required (PR): None
User Interaction (UI): None
Scope (S): Changed
Confidentiality (C): High
Integrity (I): High
Availability (A): High
Those responsible for the finding were researchers from the cybersecurity firm, who reported the bug to the plugin developers who quickly corrected the vulnerability with the update to version 5.3.2.
The vulnerability allows Contact Form to bypass any file format restrictions and allow an attacker to upload a malicious executable on a site that has file upload enabled and runs an outdated version of the plugin. This would allow the attacker to perform various actions, such as injecting a malicious script into a site, taking control of it, or performing defacement.
Update WordPress Contact Form 7 Plugin Immediately
Contact form has been published 7 5.3.2. This is an urgent maintenance and security release. We strongly recommend that you update it immediately.
We were able to use a double extension plus a Unicode character to pass a single security check, the wpcf7_antiscript_file_name.
This feature was only one of many security measures in place for the download process, and bypassing it did not allow downloading files with extensions that would work on any of our test setups.
CVE-2020-35489: Unrestricted File Upload Vulnerability
An unrestricted file upload vulnerability has been found in Contact Form 7 5.3.1 and earlier versions. Using this vulnerability, a forms submitter can bypass Contact Form 7 file name sensitization and upload a file that can be run as a script file on the host server.

The CVE-2020-35489 vulnerability allows you to bypass any file format restrictions. Therefore, an attacker can upload a malicious file, such as a script, take control of the web page, or perform a defacement.
It is recommended that all websites that have this plugin installed the updated version, in order to protect them from cybercriminals.
This is further proof that the professional maintenance of websites is important, in addition to the fact that relevant cybersecurity processes must prevail, from awareness-raising and pentesting to training organizations.
Contact Form 7

Site owners or administrators using this plugin are advised to install the latest update wordpress contact form 7 plugin as soon as possible.
Contact Form 7 alternatives
In terms of security There are several secure alternatives to Contact Form 7. like
- Ninja Forms,
- Gravity Forms,
- Visual Form Builder plugins.
Contact Form 7 Conditional Fields
See Our Related Posts:
